Introduction
Sadly we are all plagued by spam emails. An whatever steps we take, they still keep coming. Below we explain where spam comes from and some things you can do to try and reduce its volume.
What is email spam?
Email spam, also known as junk email, is unsolicited bulk messages sent through email and is a growing problem faced by most email users.
Recipients of spam often have had their email addresses obtained by spambots, which are automated programs that crawl the internet looking for email addresses.
Spammers then use these spambots to create email distribution lists. A spammer typically sends an email to millions of email addresses, with the expectation that only a small number will respond or interact with the message.
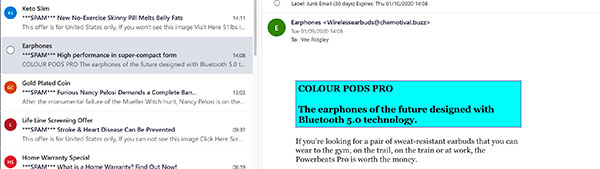
Types of spam
Spam comes in various forms, with the most popular being to promote outright scams or marginally legitimate business schemes. It can be used to promote access to inexpensive pharmaceutical drugs, weight loss programs, online gambling or to obtain personal information or money.
Other types of spam are known as ‘phishing’. These are emails disguised, often very convincingly, as official communication from genuine businesses. For example banks, credit card companies, online payment processors such as PayPal, or any other organisations a user may normally trust.
Phishing emails typically direct recipients to a fake version of the organisation’s website. Here the user is prompted to enter personal information, such as login and credit card details.
Most companies encourage you to report phishing emails to them.
https://www.gov.uk/report-suspicious-emails-websites-phishing
Most large organisations have the following email accounts set up:
phishing@comanyname.com
spam@comanyname.com
Also be aware of scam texts, that if clicked on, can enter your device and impact on your email account.
Why do I get so much spam?
‘Botnets’ allows spammers to use command-and-control servers (or C&C servers), to both gather email addresses and to distribute spam.
‘Snowshoe‘ spam is the technique of using a wide range of IP addresses and email addresses with neutral reputations to distribute spam widely.
Another method that spammers use is called ‘blank‘ email spam. This involves sending an email with an empty message body and subject line. The technique could be used in a directory harvest, or an attack against an email server that seeks to validate email addresses for a distribution list by identifying invalid bounced addresses. In this type of attack, the spammer does not need to enter text into the email.
In other instances, seemingly blank emails may hide certain viruses and worms that can be spread through HTML code embedded in the email.
Over time, spammers have developed methods to obfuscate the nature of their unsolicited email or find a way to bypass spam filters. Because spam-filtering programs often search for certain patterns or words in the subject lines and message bodies of email, spam emails often contain misspelled words or extra characters such as question marks or exclamation marks.
With ‘image spam‘, the text of a message is stored as a JPEG or GIF file and placed into the email body. The text is often computer-generated and unintelligible to human readers. This method attempts to avoid detection from text-based spam filters. Some newer spam filters now have the ability to read images and locate text in them; however, this can inadvertently filter out non-spam emails that happen to contain images featuring text.
How do I prevent Spam?
Unfortunately receiving some spam is unavoidable, for instance, if the email account used for spam is legitimate (i.e. it is a hacked email account), then spam programs will err on the side of caution and treat it as a normal email.
Our dedicated servers based here in the UK, use spam protection software to typically reduce the spam emails you receive by as much as 90%, but cannot fully eradicate spam emails due to a number of reasons as mentioned above in this article.
You can help to reduce the amount of spam that makes it into your own inbox though
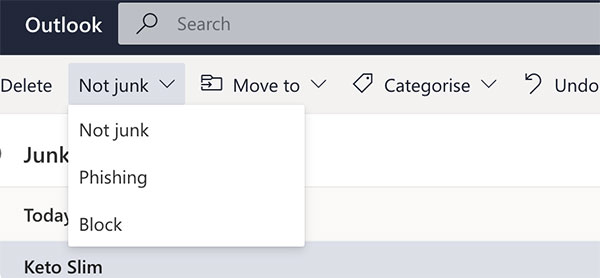
Most email client programs such as Outlook, already have spam filtering in place, which will move suspicious emails to a separate junk folder.
By reporting, blocking and deleting instances of spam email that do make it into you inboxes, you can train the email client program to prevent further messages from those particular spam addresses or messages displaying similar content going into your inbox.
For extra protection, you can also add a third-party anti-spam filter such as McAfee or Norton that will plug-in their spam program to your local email client software, which you can then adjust the sensitivity of the spam software to suit your needs.
You could also create an email whitelist, to include all of the specific email addresses, IP addresses or domains that you user trust and are therefore willing to receive email from. But this whitelist must be thoroughly and continuously updated, and it can be a time-consuming and difficult process.
Unfortunately, as all email clients are different we cannot give instructions on how to set up a whitelist, but a Google search will help you find them.
Protect your devices that have your email accounts on
We would always recommend using trusted and reputable Internet Security software such as McAfee Total Protection or Norton 360. These provide complete security protection of your devices and have built-in email spam programs that plug-in to your email client software for added protection.
Another excellent internet security tool is Malwarebytes Professional, which offers protection against Malware, Ransomware and Exploits. It is ideal to use alongside a program like McAfee Total Protection and Norton 360. To give maximum protection against all commonly known threats.
Whilst nothing is 100% guaranteed, due to new threats being found daily, paid subscription software will automatically protect you as soon as the threat is found.
Free security programs often do not have the features of paid security programs and therefore do not offer full protection. This is why we do not allow clients to connect to our systems with free versions of these programs.
See our Full Terms & Conditions, section 3.11 Passwords & Security.
Many online retailers such as Amazon or eBay sell these paid subscription Internet security software programs for a fraction of the price that you would pay if you went direct to the developer. But make sure you buy from a reputable source. If you need any guidance please let us know via your support board.
These paid subscription-based security solutions often have compete protection against viruses, spam emails and trojans, and also have advanced firewall protection and VPN’s that prevent hackers from gaining information such as email passwords that may be stored on your device.
If you think an email looks suspicious in any way, do not open it, click on any links, open any attachments or click on any images, however tempting.
If you do, it is more than likely that this will allow the spammer to put hidden malware, spyware or viruses on your computer hard drive, which can then steal important information and monitor what you are doing.
If you suspect that your email account has been compromised, you must inform us straight away, via your support board, so that we can perform a check and supply a new password.
You must also run a thorough check of your system for any malicious software. Do this using Malwarebytes Professional, and in safe mode if you can.
If an email account that is on our server is used for sending unsolicited emails, this will ‘blacklist’ your entire domain. Thus preventing all other email users at your company from sending or receiving emails. Additionally there will be a charge for us to ‘clean’ your email account and have it whitelisted again.
How are we helping to reduce your spam emails?
There is only so much that we can do to reduce your spam. The rest is for you to ensure you have adequate anti-spam software in place and follow our advice in this article.
We use a fully managed dedicated server to host your emails. What does this mean? This means only our customers are on this server and it is not shared with anyone else. As we have monitoring software in place, this allows us to keep an eye on any unusual activity.
Plus, as the server is fully managed by our hosting provider, all critical security updates and patches are applied by qualified technicians so that the server is protected against the latest cyber threats.
There are also double spam filters on the server which are activated to the recommended setting and firewall protection to help prevent hackers gaining access.
Why does spam still get through to my inbox?
Although we use a variety of anti-spam measures before you receive your emails, some will inevitably get through.
This is mainly because spammers often use legitimate email addresses that have been hacked and therefore the anti-spam software treats it as normal email.
Where spam software is unsure, it will often send it to your spam folder, where you are able to take the most appropriate action.
No anti-spam software will filter 100% of spam messages.
How can I prevent my own emails from being treated as spam?
Firstly, ensure all your security software, operating system and mail client (e.g. Outlook), are always fully up to date.
This will help to ensure your own email account is not hacked through the device you are using.
We also recommend that you do not write your email message or the email subject header in capital letters. This is because capital letters are classed as ‘internet shouting’ and is often seen as spam and as such will most likely be treated as spam.
Ensure that you do not attach any attachments carrying viruses or content that can be construed as malicious.
And finally, see our Knowledge Base article Some Emails Are Not Received By The Recipient.
Email Safety
We have all been told time and time again that, if you are unsure, then do not open the message or any attachments.
However, as spammers are getting more sophisticated, a larger proportion of spam messages are looking like they are legitimate. They appear to have come from your bank, large organisations such as Microsoft, Google, HMRC and Amazon. Or even from companies you have never dealt with, asking for you to pay a bill, or to acknowledge an attached order, etc.
Do not use the ‘Unsubscribe’ link in these emails. It lets them know you have reacted to it so your email address is genuine.
At the time of writing there is a new type of email doing the rounds. The email appears to be from Netflix or your mobile phone company. It states that they were unable to take your last payment. Followed by a button asking you to update your bank details…
Obvious signs that an email will most likely be spam or phishing:
- Where the email has come from? Is it from the legitimate URL of the business?
- Has the email address got an obvious spelling error or additional character, for instance @lloyds-bank.com as opposed to @lloydsbank.com.
- Do you even have an account with the business the email is claiming to be from?
- Is the email from a gmail.com address or hotmail.com, outlook.com, rather than the company’s legitimate URL?
Other signs are that any hyperlinks within the message are, when you hover your cursor over them, are trying to send you to a fake website. Or asking you to provide sensitive information such as bank details, security details, etc.
Here is a useful article with even more information: https://www.itgovernance.co.uk/blog/5-ways-to-detect-a-phishing-email
Attachments are often not named correctly or in a format that your computer does not recognise and cannot therefore convert to Microsoft Word, Excel or Adobe PDF.
When you delete the message, remember to also delete it from your deleted items folder.
